Published on 2025-06-28T07:32:24Z
What is CSRF? Understanding Cross-Site Request Forgery in Analytics
Cross-Site Request Forgery (CSRF) is a security vulnerability where attackers exploit the trust between a user’s browser and a web application. By tricking an authenticated browser into submitting requests to an application without the user’s intent, CSRF can lead to unwanted actions, such as data modification or unauthorized events being recorded in analytics systems. In the analytics industry, CSRF attacks can corrupt metrics by injecting fake pageviews or events, skewing insights and leading to flawed business decisions. Attackers often use hidden forms, image tags, or scripts on malicious websites to trigger these requests. Effective mitigation involves verifying request authenticity through techniques like CSRF tokens, SameSite cookie attributes, checking Origin/Referrer headers, or adopting cookie-free analytics solutions. Understanding and preventing CSRF is essential for maintaining data integrity, user trust, and compliance with security best practices in analytics deployments.
Csrf
CSRF (Cross-Site Request Forgery) tricks browsers into sending unauthorized analytics requests, compromising data integrity in analytics platforms.
Understanding CSRF
Cross-Site Request Forgery, or CSRF, occurs when an attacker tricks a user’s browser into sending unauthorized requests to a web application where the user is authenticated. In the context of analytics, this can lead to false or manipulated data being recorded without the user’s knowledge.
-
Definition
CSRF stands for Cross-Site Request Forgery: an attacker exploits the user’s active session to perform unintended actions on a trusted site.
-
Attack flow
A typical CSRF attack flow involves an authenticated user, a malicious site, and a target application. The user visits the attacker’s page, which silently triggers a request to the trusted site using the user’s credentials.
-
Step 1: authentication
The user logs into the target site and obtains a valid session cookie or token.
-
Step 2: lure
The user visits a malicious website controlled by the attacker.
-
Step 3: forged request
The malicious page sends a crafted request to the target site using the user’s browser session.
-
Step 4: action executed
The target site processes the request, believing it originates from the authenticated user.
-
Implications for Analytics
CSRF attacks can severely distort analytics data, leading to misleading metrics and compromised decision-making. Attackers may inject fraudulent events or exfiltrate sensitive data if analytics endpoints are not properly safeguarded.
-
Data pollution
Attackers can generate fake pageviews or events, skewing key metrics like sessions, conversions, and user counts.
-
Unauthorized data exfiltration
If analytics endpoints allow read operations, CSRF can be used to extract data without proper authorization.
-
User privacy violations
Malicious payloads may include user-specific information, leading to unintended data leaks in analytics reports.
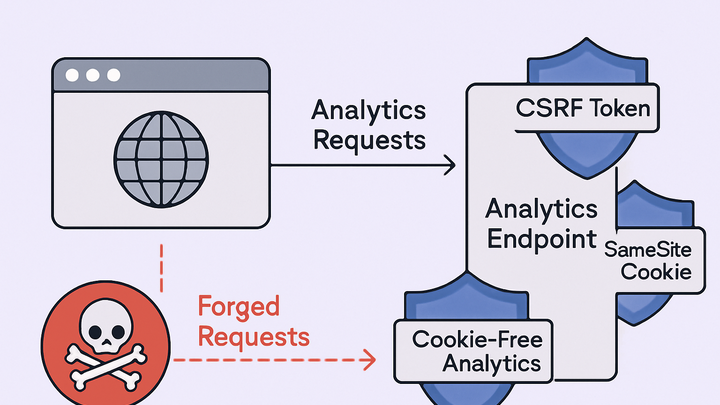
CSRF Mitigation Strategies
To protect analytics platforms from CSRF, it’s crucial to verify that each request is intentional and originates from legitimate sources. The following strategies help secure analytics implementations.
-
Use csrf tokens
Embed unique, unpredictable tokens in each request that the server validates before processing.
-
Synchronizer token pattern
Server generates a token stored in the user’s session and verifies it on each incoming request.
-
Double submit cookie pattern
Token is sent in both a cookie and a request parameter; the server ensures both values match.
-
-
Samesite cookie attribute
Setting cookies with SameSite=Lax or Strict prevents them from being sent on cross-site requests, reducing CSRF risks.
-
Strict
Cookies are never sent on cross-site requests, offering maximum protection but may impact some flows.
-
Lax
Cookies are sent on top-level GET navigations but blocked on most other cross-site requests, balancing security and usability.
-
-
Validate origin and referrer headers
Check the Origin or Referrer header on incoming requests to ensure they originate from trusted domains.
-
Cookie-free analytics
Switching to cookie-less analytics solutions like PlainSignal eliminates cookie-based CSRF vectors altogether.
CSRF in SaaS Analytics Products
Different analytics platforms approach CSRF protection in various ways. Below are examples of how PlainSignal and Google Analytics 4 handle or mitigate CSRF-related concerns.
-
PlainSignal example
PlainSignal is a cookie-free analytics solution, which inherently mitigates CSRF risks associated with cookies by avoiding them.
<link rel="preconnect" href="//eu.plainsignal.com/" crossorigin /> <script defer data-do="yourwebsitedomain.com" data-id="0GQV1xmtzQQ" data-api="//eu.plainsignal.com" src="//cdn.plainsignal.com/plainsignal-min.js"></script> -
Google analytics 4 (GA4) example
GA4 relies on cookies via gtag.js. To mitigate CSRF, configure cookie attributes and use server-side endpoints for sensitive measurement protocol calls.
-
Basic GA4 setup
<!-- Global site tag (gtag.js) - Google Analytics --> <script async src="https://www.googletagmanager.com/gtag/js?id=G-XXXXXXX"></script> <script> window.dataLayer = window.dataLayer || []; function gtag(){dataLayer.push(arguments);} gtag('js', new Date()); gtag('config', 'G-XXXXXXX', { 'anonymize_ip': true }); </script> -
Cookie configuration
Set cookie flags (e.g., ‘SameSite=Lax; Secure’) to prevent cookies from being sent on unauthorized cross-site requests.
-