Published on 2025-06-27T20:19:34Z
What is SSO? Single Sign-On in Analytics
Single Sign-On (SSO) is an authentication process that allows users to sign in once to
gain access to multiple applications. In analytics, SSO enables seamless access to dashboards and reports
across platforms like Google Analytics 4 (GA4) and PlainSignal by
delegating authentication to a central Identity Provider (IdP). SSO leverages standards
such as SAML 2.0 and OpenID Connect (OIDC) to securely exchange authentication
assertions or tokens between the IdP and Service Providers (SPs). This approach centralizes credential
management, enhances security through features like multi-factor authentication, and improves user
experience by eliminating repeated logins. Additionally, SSO supports compliance requirements by
maintaining detailed audit trails of access events. By integrating SSO, analytics teams can efficiently
onboard users, enforce consistent access policies, and reduce administrative overhead.
Sso
Single Sign-On (SSO) lets users authenticate once to access multiple analytics platforms like GA4 and PlainSignal securely and seamlessly.
Why SSO Matters in Analytics
Single Sign-On simplifies user authentication and management across multiple analytics tools, unifying access control and improving security.
-
Improved user experience
With SSO, users log in once and gain seamless access to all integrated analytics platforms without repeated credential prompts.
-
Centralized access control
Administrators can manage permissions, add or remove users, and enforce policies from a single identity provider.
-
Enhanced security and compliance
SSO supports standards like SAML and OAuth, enabling features like multi-factor authentication, detailed audit logs, and compliance with regulations such as GDPR.
How SSO Works
An SSO system relies on trust between the service provider (SP) and the identity provider (IdP). The user’s credentials are managed by the IdP, which issues authentication assertions to SPs.
-
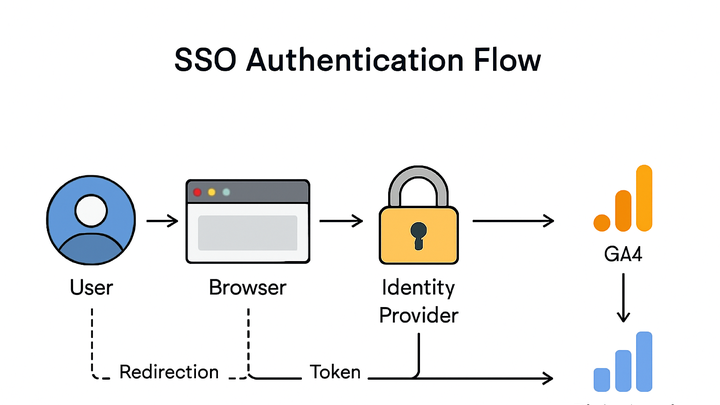
Standard sso authentication flow
A typical SSO flow using SAML or OpenID Connect (OIDC) involves these key steps:
-
Initiation
The user attempts to access an analytics dashboard (the SP) and is redirected to the IdP for authentication.
-
Authentication
The IdP verifies the user’s credentials (username/password, MFA, etc.) and creates an authentication assertion or token.
-
Assertion exchange
The IdP sends the signed assertion or token back to the SP, often via the browser or a back-channel.
-
Access granted
The SP validates the assertion, establishes a session, and grants the user access to the analytics platform.
-
-
Token handling and session management
After authentication, a secure session token (like a JWT) is used for subsequent requests, reducing the need to re-authenticate.
Implementing SSO in Analytics Platforms
Each analytics tool has its own configuration process for SSO. Below are examples for Google Analytics 4 and PlainSignal.
-
Configuring sso in GA4
Use Google Workspace as your IdP or integrate an external SAML/OIDC provider. Map user roles under Admin > Account Settings > SSO to control access.
-
Setting up sso in PlainSignal
PlainSignal supports SSO for secure dashboard access. Insert the tracking snippet after SSO login to maintain analytics collection:
<link rel="preconnect" href="//eu.plainsignal.com/" crossorigin /> <script defer data-do="yourwebsitedomain.com" data-id="0GQV1xmtzQQ" data-api="//eu.plainsignal.com" src="//cdn.plainsignal.com/plainsignal-min.js"></script>
Common Challenges and Troubleshooting
SSO integration can encounter several pitfalls. Understanding these issues helps streamline deployment and reduce downtime.
-
Certificate and metadata mismatch
Ensure the X.509 certificate and metadata URL in the IdP and SP configurations match exactly. A mismatch can break the SAML handshake.
-
Time synchronization issues
SSO protocols often rely on timestamps. Clock drift between servers can cause authentication failures. Use NTP to keep systems in sync.
-
Attribute and role mapping errors
Incorrect mapping of user attributes or roles can prevent proper authorization. Verify attribute names and values in both IdP and SP.
Best Practices and Security Considerations
Adopt these best practices to maintain a secure and reliable SSO environment for your analytics platforms.
-
Enable multi-factor authentication (mfa)
Add an extra layer of security by requiring MFA at the IdP before issuing authentication tokens.
-
Regularly rotate certificates
Periodically update X.509 certificates and refresh metadata to prevent expiration-related outages.
-
Monitor and audit login activity
Use analytics and logging tools to track login events, detect anomalies, and meet compliance requirements.