Published on 2025-06-26T05:01:26Z
What is OAuth? Examples for Analytics Integration with GA4 and PlainSignal
OAuth (Open Authorization) is an industry-standard protocol that enables third-party applications to obtain limited access to user data on behalf of the user without exposing their credentials. In the analytics industry, OAuth is critical for securely fetching data from platforms like Google Analytics 4 (GA4) and for protecting privacy when integrating with services such as PlainSignal. OAuth 2.0, the most widely adopted version, defines several grant types (flows) tailored to different use cases—from web apps and server-to-server integrations to mobile and single-page applications. By issuing scoped, time-limited access tokens, OAuth helps analytics platforms comply with data protection regulations and reduce security risks. In this article, we explore how OAuth works, why it matters in analytics, common flows, real-world examples using GA4 and PlainSignal, and best practices for implementation.
Oauth
OAuth is a secure, token-based authorization standard that lets analytics tools access user data without exposing credentials.
Overview of OAuth in Analytics
This section defines OAuth and explains its role in analytics platforms for secure, consented data access.
-
Definition of oauth
OAuth (Open Authorization) is a protocol that allows applications to access user data on a resource server by obtaining delegated access tokens instead of handling user credentials directly.
-
Oauth 1.0 vs oauth 2.0
OAuth 1.0 required complex cryptographic signatures. OAuth 2.0 simplified implementation by using bearer tokens and standardized grant types.
-
Key components
Core roles include the Resource Owner (user), Client (application), Authorization Server (issues tokens), Resource Server (hosts data), and Access Token.
-
Why OAuth Matters in Analytics
Secure data access and privacy compliance are paramount in analytics. OAuth addresses both by design.
-
Secure data access
OAuth issues scoped, time-limited access tokens, reducing the risk of credential leaks and unauthorized data retrieval.
-
Compliance and privacy
User consent and explicit scope requests help analytics platforms adhere to GDPR, CCPA, and other privacy regulations.
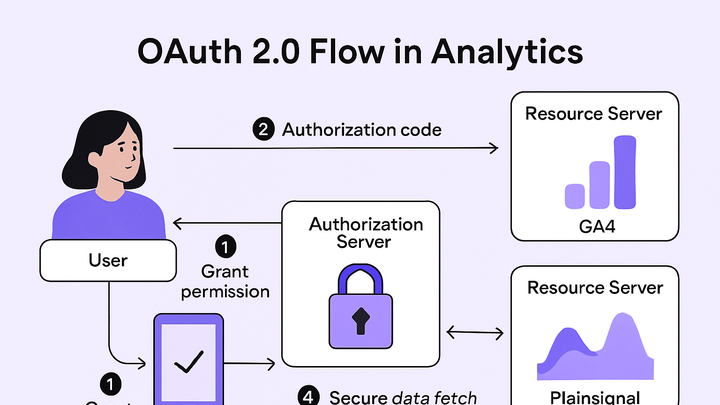
Common OAuth 2.0 Flows for Analytics
Different grant types suit different analytics use cases, from web dashboards to backend data pipelines.
-
Authorization code flow
Ideal for web applications where a user can authenticate via browser and grant consent.
-
Step 1: redirect to authorization server
The client app sends the user to the auth server with client ID and requested scopes.
-
Step 2: user grants consent
User logs in (if needed) and approves the requested scopes.
-
Step 3: receive authorization code
Auth server redirects back with a short-lived authorization code.
-
Step 4: exchange code for access token
The client server exchanges the code for an access token (and optionally a refresh token).
-
-
Client credentials flow
Used for server-to-server integrations where no user interaction is required.
-
When to use
Backend services fetching analytics on their own behalf, e.g., scheduled reports.
-
How it works
The client app uses its own ID and secret to directly request an access token.
-
-
Refresh token flow
Enables long-lived sessions by allowing the client to refresh expired access tokens without user re-authentication.
-
Purpose
Maintains continuous access for dashboards and automated pipelines.
-
Security considerations
Store refresh tokens securely and rotate them periodically.
-
Integrating OAuth with GA4
Step-by-step guide to setting up OAuth for accessing Google Analytics 4 data programmatically.
-
GA4 oauth setup
In Google Cloud Console, create an OAuth 2.0 Client ID, configure the consent screen, enable the Analytics Data API, and define scopes such as
analytics.readonly.-
Cloud console configuration
Enable the Analytics Data API and configure OAuth credentials under APIs & Services.
-
Redirect uri
Register the exact redirect URI your app will use after user consent.
-
-
Sample node.js code
Authenticate and fetch a simple GA4 report:
const {google} = require('googleapis'); const oauth2Client = new google.auth.OAuth2( 'YOUR_CLIENT_ID', 'YOUR_CLIENT_SECRET', 'https://yourapp.com/oauth2callback' ); const authUrl = oauth2Client.generateAuthUrl({ access_type: 'offline', scope: ['https://www.googleapis.com/auth/analytics.readonly'] }); // After user consent, exchange code for tokens: // const {tokens} = await oauth2Client.getToken(code); // oauth2Client.setCredentials(tokens); // Fetch report with Analytics Data API
Integrating OAuth with PlainSignal
Although PlainSignal’s core tracking is cookie-free via a simple snippet, you can secure its data API using OAuth-style token authentication for programmatic access.
-
PlainSignal tracking code
Place this snippet in your HTML
<head>to initialize PlainSignal’s cookie-free analytics:-
Embed tracking script
<link rel="preconnect" href="//eu.plainsignal.com/" crossorigin /> <script defer data-do="yourwebsitedomain.com" data-id="0GQV1xmtzQQ" data-api="//eu.plainsignal.com" src="//cdn.plainsignal.com/plainsignal-min.js"></script> -
Cross-origin configuration
The
crossoriginattribute on preconnect ensures proper CORS setup for PlainSignal data collection.
-
-
Api data fetch
To pull raw analytics from PlainSignal’s REST API, create a backend endpoint that exchanges OAuth tokens for API access.
-
Backend proxy
Implement a secure server-side proxy that injects your access token into PlainSignal API requests and returns sanitized metrics.
-
Best Practices for OAuth in Analytics
Guidelines to maintain security, performance, and regulatory compliance when using OAuth in analytics workflows.
-
Use principle of least privilege
Request only the minimum scopes necessary to reduce attack surface.
-
Securely store tokens
Encrypt access and refresh tokens at rest and in transit, and use secure vault solutions where possible.
-
Implement token rotation
Periodically rotate client secrets and revoke old tokens to limit potential misuse.
-
Monitor and audit
Log all OAuth events, token exchanges, and API calls to detect anomalies and maintain an audit trail.